Social engineering is a manipulation technique used by hackers to trick users into exposing private or confidential information such as passwords or bank accounts. Cybercriminals take advantage of users' ignorance or carelessness in order to bribe or steal.
Digital attacks on users and organizations are the order of the day: only a few years ago, the in Mexico there are more than 78,000 cyber-attacks per hour and in 40,000 attacks occur every day in Spain. These negative actions are known as social engineering and there are several types that threaten the confidential information and privacy of individuals and companies.
Fortunately, just as there are attacks, there are also solutions to social engineering. In this content we will analyze everything relevant to cyber-attacks and the way in which an average company or user can protect themselves against them.
What is social engineering?
Social engineering is a manipulation technique done by hackers that seeks to trick users into exposing private or confidential information such as passwords, bank accounts or allowing hidden malware downloads to take control of the computer.
Cybercriminals take advantage of users' ignorance or carelessness in order to bribe or steal. In the first case, by disrupting or corrupting data to cause damage or inconvenience and in the second case, to obtain something in return such as money, access or information.
8 types of social engineering
To the misfortune of companies and users, there are many types of social engineering that can be applied; all with the same intention: to cause harm and get something in return. The most common are the following:
1. Phishing or identity theft
Phishing is one of the most common social engineering attacks and consists of cybercriminals posing as trusted brands, banks or institutions in an attempt to manipulate users into providing information such as logins, passwords or downloading malicious or extortion software. Among its variants are:
- Fisherman of phishing is the use of fake customer service accounts on social networks.
- Spear phishing are attacks of phishing targeted at specific companies or users.
- Whaling does not target average users, but seeks to deceive high-level business executives, such as CEOs or CFOs.
This attack usually occurs when receiving fraudulent emails claiming to be a reliable source; with this they seek to obtain confidential data such as full name, date of birth or account number to verify the user's identity. If people are unaware or careless, these cybercriminals can steal private data.
Vishing and Smishing
Unlike phishing, which is an attack carried out directly by e-mail, these types of social engineering make use of voice and text to try to steal information.
In the case of vishing, the cybercriminal attempts to trick the user into revealing confidential information or giving access to their computer or other device over the phone. In this attack the scammer scares, intimidates or threatens the victim to get what he wants. It is a very common type of attack, which, for example in Mexico, has had an increase of 5 % and the most affected are usually older adults.
The smishing uses the same techniques as the phishing and the vishingbut by text message.
3. Diversion theft
This type of social engineering targets deliverymen or couriers to travel to the wrong destination and deliver the package to the wrong person. This attack is carried out cyber-physically by stealing confidential data and tricking the victim into sending or sharing someone else's information (to whom the fraudster directs).
4. Pretext
This is a social engineering technique in which the attacker creates a false scenario, where the victim feels compelled to cooperate under false pretenses (hence the name). For example, a scammer may impersonate a police officer, auditor or a senior manager of a company to intimidate another person and force them to share the requested confidential information.
5. Baiting
Baiting is also a very common type of social engineering, in which victims are asked to provide confidential information in exchange for a gift. For example, a user may log in to their email and see that they have a message promising a free item or a discount card in exchange for answering a simple survey or filling out a form.
When the user accepts, he/she is usually redirected to a fake website, where he/she must provide his/her email and password, and under this deception provides his/her confidential information. The cybercriminal then uses this data to send malicious software.
6. Quid pro quo
In Quid pro quo or "Something for something" (from its Latin meaning) the fraudster impersonates a member of a company to deceive an employee in order to obtain internal access.
For example, an attacker may pose as a technician in the IT department and call the company's extensions to offer support. He tries this until he finds someone who is in a situation where he needs support; he is attentive and asks the employee for his logins so that he can fix his problem.
7. Honey Trap
This attack makes use of the feelings and emotions of the victims, since its objective is to start a sentimental relationship and then persuade people to share confidential information or pay large sums of money.
8. Trough
In this type of social engineering, the cybercriminal knows which websites are usually visited by his targets and then infects them, so that when the user logs in or provides his access data, he can capture them in order to breach your network or install a Trojan virus to access your network.
3 examples of social engineering
- Phishing e-mail.
- Honey trap in dating app.
- Extortion by WhatsApp.
1. Phishing e-mails
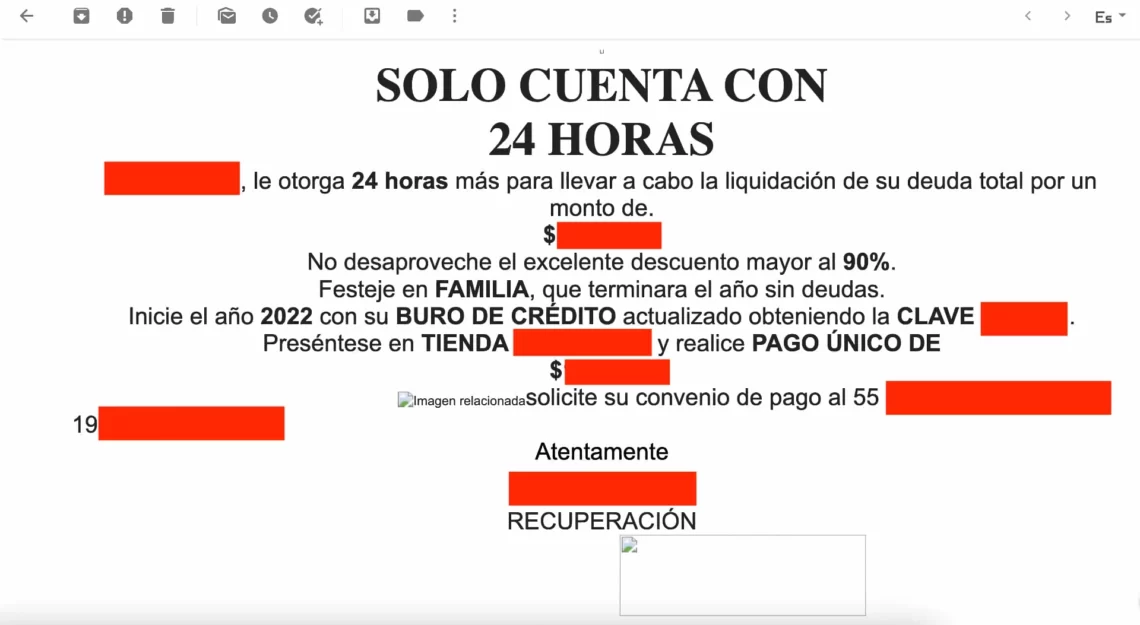
This social engineering is one of the most common and is aimed mainly at average users. In this example we can see an email message inviting the user to settle a supposed debt with a department store. However, what the attackers want to achieve is that the person dials the number provided to provide personal information.
Phishing e-mails usually have common factors: they use intimidating language, often have cacographs or errors in their design; the logos of the companies they impersonate are of poor quality or are old designs no longer used by the company. In addition, the email account does not come from an official institution.
2. Honey trap in dating app
If you've seen the recent Netflix documentary "The Tinder Scammer." you will know exactly where we are going with this example of social engineering. This production follows the case of 3 women who were scammed by a man they met on the dating app Tinder.
With very similar stories, this criminal poses as the son of a millionaire and after some time of conquest and persuasion, convinces his victims to give him large sums of money. While we would like to give more details of this documentary, we do not want to fall into spoilers. However, these attacks are also common and in 2021 alone this kind of scammers have collected around 600,000 USD.

3. Extortion by WhatsApp
The specialized portal WABetainfo alerted in 2021 about a new form of smishing-type extortion, but through the WhatsApp messaging platform. The scammer sends the following message: "Sorry, who are you? I found you on my contact list" and if the person decides to answer, the scammer tries to continue the conversation to gain their trust and obtain personal data.
The questions are very common and can be taken as any other conversation in which you meet someone, for example: name, age and occupation; all accompanied by a friendly and innocent tone. The objectives of this type of social engineering are to get the victim to share their social network accounts in order to obtain more information and photographs.

What is a social engineering attack?
A social engineering attack is the whole process that a cybercriminal carries out to obtain something from his victims in exchange; for example, access to personal, bank or corporate accounts, personal or confidential information or the download of some malicious software to do internal damage in the network.
The first step of a social engineering attack is the prior research that the fraudster performs on his targets. If the victim will be a company, the hacker makes a thorough reconnaissance of the entire organizational structure, internal operations and form of communication.
A cybercriminal pays close attention to the behavior and patterns of the different employees that the company has: from the first level to the managers. They can obtain the information from social networks and from the online and offline analysis of users. When the attacker obtains all the necessary information, he structures his plan and sets it in motion with the intention of gaining access to personal information or causing damage to the company's internal network.
How to prevent a social engineering attack?
- Use multifactor authentication.
- Set high spam filters.
- Use VPN.
- Maintain software up to date.
- Constantly monitor systems and networks.
- Use cloud-based WAF.
1. Use multifactor authentication
It is important that online accounts have more than just a password for protection. Multifactor authentication adds more layers of security to verify identity when accessing an account. These factors can be fingerprints, facial recognition or temporary codes sent to the private mobile device. This way, any cybercriminal trying to access this account will not be able to do so; at least not as easily.
2. Set high spam filters
Although all e-mail messaging services have the spam folder activated, it is best to verify that the level is high to prevent malicious messages from flooding the main inbox. Just remember to constantly check that some real or important message has not fallen there by mistake.
3. Use VPN
A virtual private network (VPN) can prevent anyone who wants to access someone else's main network from doing so. These services provide a private, encrypted tunnel into any Internet connection used. Thus, not only is the connection protected, but also personal data and information becomes anonymous and untraceable. This is functional even for browsing where third party cookies are used.
4. Keep software up to date
When software is kept up to date when a new version is available, it remains protected and ensures essential security fixes to safeguard your information. When updates are delayed or skipped, it leaves a security hole that cybercriminals can exploit to attack and exploit this vulnerability.
5. Constantly monitor systems and networks
It is important that systems are monitored 24 hours a day, especially those that house confidential information. This requires both external and internal scans to find vulnerabilities in the network. This process can also identify fake domains and remove them instantly to prevent a data breach.
6. Use cloud-based WAF
A Web Application Firewall (WAF) cloud-based firewall offers more protection than a conventional firewall, as it is designed to ensure maximum protection against social engineering attacks. They can constantly monitor applications or websites for anomalies or misbehavior. If it detects anything negative, it blocks attacks instantly and issues alerts about any attempt to install malware.
It should never be taken for granted that you will never suffer a social engineering attack, as there are many variants that focus on different targets. One of them can be an employee, a social network user or even the director of a prestigious company. The best thing to do is to stay alert and think before clicking or sharing confidential information to anyone, by any means whatsoever.




